1. Introduction to Foreman
Foreman is a centralized tool for provisioning, content delivery, remote management, and monitoring of multiple Enterprise Linux deployments. With Foreman, you can deploy, configure, and maintain your systems across physical, virtual, and cloud environments.
2. Content and patch management with Foreman
With Foreman, you can provide content and apply patches to hosts systematically in all lifecycle stages.
2.1. Content flow in Foreman
Content flow in Foreman involves management and distribution of content from external sources to hosts.
Content in Foreman flows from external content sources to Foreman server. Smart Proxy servers mirror the content from Foreman server to hosts.
- External content sources
-
You can configure many content sources with Foreman. The supported content sources include the Red Hat Customer Portal, custom Deb and Yum repositories, PyPI, Git repositories, Ansible collections, container registries, SCAP repositories, or internal data stores of your organization.
- Foreman server
-
On your Foreman server, you plan and manage the content lifecycle.
- Smart Proxy servers
-
By creating Smart Proxy servers, you can establish content sources in various locations based on your needs. For example, you can establish a content source for each geographical location or multiple content sources for a data center with separate networks.
- Hosts
-
By assigning a host system to a Smart Proxy server or directly to your Foreman server, you ensure the host receives the content they provide. Hosts can be physical or virtual.
2.2. Content views in Foreman
A content view is a deliberately curated subset of content that your hosts can access. By creating a content view, you can define the software versions used by a particular environment or Smart Proxy server.
Each content view creates a set of repositories across each environment. Your Foreman server stores and manages these repositories. For example, you can create content views in the following ways:
-
A content view with older package versions for a production environment and another content view with newer package versions for a Development environment.
-
A content view with a package repository required by an operating system and another content view with a package repository required by an application.
-
A composite content view for a modular approach to managing content views. For example, you can use one content view for content for managing an operating system and another content view for content for managing an application. By creating a composite content view that combines both content views, you create a new repository that merges the repositories from each of the content views. However, the repositories for the content views still exist and you can keep managing them separately as well.
- Default Organization View
-
A Default Organization View is an application-controlled content view for all content that is synchronized to Foreman. You can register a host to the Library environment on Foreman to consume the Default Organization View without configuring content views and lifecycle environments.
You can access unprotected repositories in the Default Organization View content view. The URL consists of your Smart Proxy FQDN,
/pulp/content/, your organization label,/Library/custom/, your product label,/, your repository label, and a trailing/, for example,https://foreman.example.com/pulp/content/Example/Library/custom/AlmaLinux_9/BaseOS/. - Promoting a content view across environments
-
When you promote a content view from one environment to the next environment in the application lifecycle, Foreman updates the repository and publishes the packages.
The repositories for Testing and Production contain the my-software-1.0-0.noarch.rpm package:
| Development | Testing | Production | |
|---|---|---|---|
Version of the content view |
Version 2 |
Version 1 |
Version 1 |
Contents of the content view |
my-software-1.1-0.noarch.rpm |
my-software-1.0-0.noarch.rpm |
my-software-1.0-0.noarch.rpm |
If you promote Version 2 of the content view from Development to Testing, the repository for Testing updates to contain the my-software-1.1-0.noarch.rpm package:
| Development | Testing | Production | |
|---|---|---|---|
Version of the content view |
Version 2 |
Version 2 |
Version 1 |
Contents of the content view |
my-software-1.1-0.noarch.rpm |
my-software-1.1-0.noarch.rpm |
my-software-1.0-0.noarch.rpm |
This ensures hosts are designated to a specific environment but receive updates when that environment uses a new version of the content view.
With Distribute archived content view versions enabled, you can access unprotected repositories in published content view versions.
The URL consists of your Smart Proxy FQDN, /pulp/content/, your organization label, /content_views/, your content view, your content view version, /custom/, your product label, /, your repository label, and a trailing /, for example, https://foreman.example.com/pulp/content/Example/content_views/AlmaLinux_9/2.1/custom/AlmaLinux_9/BaseOS/.
If you want to access the latest published content view, the URL consists of your Smart Proxy FQDN, /pulp/content/, your organization label, your lifecycle, your content view, /custom/, your product label, /, your repository label, and a trailing /, for example, https://foreman.example.com/pulp/content/Example/Production/AlmaLinux_9/custom/AlmaLinux_9/AlmaLinux_9/.
2.3. Lifecycle environments and environment paths
Application lifecycles are divided into lifecycle environments which represent each stage of the application lifecycle. By linking lifecycle environments, you create an environment path.
You can promote content along the environment path to the next lifecycle environment when required. When you promote a content view from one environment to the next environment in the application lifecycle, Foreman updates the repository and publishes the packages. For example, if development ends on a particular version of an application, you can promote this version to the testing environment and start development on the next version.
2.4. Content types in Foreman
With Foreman, you can import and manage many content types. You can use any custom content and content from Red Hat, Canonical, Oracle, and SUSE.
For example, Foreman supports the following content types:
- RPM packages
-
Import RPM packages from any repository, for example from Amazon, Oracle, Red Hat, SUSE, and custom repositories. Foreman server downloads the RPM packages and stores them locally. You can use these repositories and their RPM packages in content views.
- Deb packages
-
Import Deb packages from repositories, for example, for Debian or Ubuntu. You can also import single Deb packages or synchronize custom repositories. You can use these repositories and their Deb files in content views.
- Kickstart trees
-
Import the Kickstart trees to provision a host. New systems access these Kickstart trees over a network to use as base content for their installation. Foreman contains predefined Kickstart templates. You can also create your own Kickstart templates.
- Provisioning templates
-
Templates to provision hosts running EL based on synchronized content and Debian, Ubuntu, or SUSE Linux Enterprise Server based on local installation media. Foreman contains predefined AutoYaST, Kickstart, and Preseed templates as well as the ability to create your own, which are used to provision systems and customize the installation.
- ISO and KVM images
-
Download and manage media for installation and provisioning. For example, Foreman downloads, stores, and manages ISO images and guest images for specific Red Hat Enterprise Linux and non-Red Hat operating systems.
- OSTree
-
Import OSTree branches and publish this content to an HTTP location for consumption by OSTree clients.
- Custom file type
-
Manage content for any type of file you require, such as SSL certificates, ISO images, and OVAL files.
3. Provisioning management with Foreman
With Foreman, you can provision hosts on various compute resources with many provisioning methods from a unified interface.
3.1. Provisioning methods in Foreman
With Foreman, you can provision hosts by using the following provisioning methods.
- Network based
-
You can use this method with hosts that are capable of PXE booting or UEFI HTTP booting.
You must configure the necessary network booting services, such as DHCP or TFTP. When you create a host entry, you select a PXE loader that can configure DHCP options for network booting if Smart Proxy is set up to configure the DHCP service automatically.
This method uses an operating system installer, such as Anaconda, Debian Installer, or YaST, and template-generated file with installation options downloaded from Foreman, such as Kickstart, Preseed, or AutoYaST.
- Network based with PXE Discovery
-
You can create host entries by discovering hosts on a network. The discovery process uses the Discovery image to boot the host and report its hardware details to Foreman. You can automate provisioning of discovered hosts by creating Discovery rules.
- PXE-less Discovery with kexec
-
You can use this method with hosts that do not support network boot.
You must configure DHCP for host discovery.
This method uses the Discovery image ISO to boot the host and report its hardware details to Foreman. Using kernel execute (kexec), the Discovery image runs the installer downloaded from Foreman.
|
Important
|
Kernel execute is a Technology Preview feature only. Technology Preview features are not supported by Foreman community. Foreman community does not recommend using them in production. These features provide early access to upcoming product features, enabling customers to test functionality and provide feedback during the development process. |
- Boot disk based
-
You can use this method with hosts that do not support network boot or when you do not have the option of configuring network booting services, such as DHCP.
This method supplies the booting capability but the rest of the provisioning process still downloads the installer and template-generated files from Foreman to automate the installation.
- Image based
-
You can use this method with virtual machines or cloud instances.
This method uses a virtual image template or a cloud image from a compute resource to provision the operating system. Foreman can customize the image by running either a pre-boot or post-boot configuration script generated from a provisioning template.
4. Expense management for Red Hat subscriptions
Red Hat provides you with several tools to control costs and optimize spending on Red Hat subscriptions. This is useful if you plan to manage Red Hat Enterprise Linux hosts.
4.1. Subscriptions usage data
For the purposes of expense management and to optimize your spending, track your subscriptions usage data that you can get from your Foreman environment and Red Hat. You can track usage, capacity, and utilization of your Red Hat subscriptions.
- Usage
-
Measures the consumption of installed Red Hat products.
This data tells you: How much am I using? For example: I have 42 hypervisors, each with 2 sockets, tagged with the Production usage type.
- Capacity
-
Measures the amount of Red Hat products that have been purchased. It is the upper limit of usage.
This data tells you: How much have I purchased? For example: I purchased QTY 52 of RH00001. Each RH00001 covers a 2-socket hypervisor and all of its guests.
- Utilization
-
Measures how much of the purchased capacity has been exhausted.
This data tells you: How much of my capacity is being used? For example: I am using 42 of my 52 RH00001, leaving 10 free for additional use.
4.2. Subscriptions tracking tools
You can track subscriptions usage by combining the following tools.
- System Purpose
-
Defines non-technical system attributes for hosts to aid accurate inventory reporting:
-
Service Level Agreement (SLA): Self-Support, Standard, Premium
-
Usage type: Production, Development/Test
-
Role: Server, Workstation
System purpose is configured by using the Subscription Manager tool.
-
- Insights client
-
Collects data from hosts and sends it to Foreman. Foreman then forwards the data and host inventory to the Red Hat Hybrid Cloud Console for analysis. You can install the Insights client on Red Hat Enterprise Linux hosts during host registration, host provisioning, or using remote execution.
- Subscriptions service
-
Provides capacity data, calculates utilization, and reports subscription usage in connected scenarios. This service is hosted on the Red Hat Hybrid Cloud Console.
- Foreman
-
Provides reports on products installed on hosts. You can download these reports in various formats, such as YAML, JSON, HTML, and CSV. You can use these reports to calculate utilization locally.
4.3. Subscriptions tracking scenarios
You can track your subscription usage in one of the following scenarios, depending on your environment and data sensitivity.
- Connected scenario
-
You share all collected data with Red Hat.
-
Foreman uploads inventory data to the Red Hat Hybrid Cloud Console automatically.
-
Red Hat Hybrid Cloud Console provides all services.
-
Services powered by Red Hat Lightspeed analyze the data.
-
Subscriptions service in the Red Hat Hybrid Cloud Console calculates utilization data.
-
- Connected data-sensitive scenario
-
You share just enough data with Red Hat to enable subscription reporting.
-
You control what data is uploaded by enabling obfuscation or exclusion settings.
-
Foreman uploads inventory data to the Red Hat Hybrid Cloud Console automatically.
-
Red Hat Hybrid Cloud Console provides limited services.
-
Subscriptions service in the Red Hat Hybrid Cloud Console calculates utilization data.
-
- Disconnected scenario
-
You do not share any data with Red Hat. Instead, you track your subscription usage as follows:
-
You can get usage data from the Host - Installed Products report in Foreman.
-
You can get capacity data from the Subscriptions service in the Red Hat Hybrid Cloud Console.
-
You can calculate utilization data locally using a tool of your choosing.
-
5. Major Foreman components
A typical Foreman deployment consists of the following components: a Foreman server, Smart Proxy servers, and hosts that receive content and configuration from Foreman server and Smart Proxy servers.
5.1. Foreman server overview
Foreman server is the central component of a Foreman deployment.
A typical Foreman deployment includes one Foreman server on which you perform the following operations:
-
Content lifecycle management
-
Configuration of Smart Proxy servers
-
Configuration of hosts
-
Host provisioning
-
Patch management
-
Subscription management
Foreman server delegates content distribution, host provisioning, and communication to Smart Proxy servers. Foreman server itself also includes a Smart Proxy.
Foreman server also contains a fine-grained authentication system. You can grant Foreman users permissions to access precisely the parts of the infrastructure for which they are responsible.
5.2. Smart Proxy overview
With Smart Proxy servers, you can extend the reach and scalability of your Foreman deployment. Smart Proxy servers provide the following functionalities in a Foreman deployment:
-
Running localized services to discover, provision, control, and configure hosts.
-
Mirroring content from Foreman server to establish content sources in various geographical or logical locations. By registering a host to a Smart Proxy server, you can configure this host to receive content and configuration from the Smart Proxy in their location instead of from the central Foreman server.
By using content views, you can specify the exact subset of content that Smart Proxy server makes available to hosts. For more information, see Content and patch management with Foreman.
5.3. Overview of hosts in Foreman
A host is any Linux client that Foreman manages. Hosts can be physical or virtual.
You can deploy virtual hosts on any platform supported by Foreman, such as Amazon EC2, Google Compute Engine, KVM, libvirt, Microsoft Azure, OpenStack, Proxmox, Rackspace Cloud Services, or VMware vSphere.
With Foreman, you can manage hosts at scale, including monitoring, provisioning, remote execution, subscription management, content management, and configuration management. You can also group hosts by using features such as host groups and host collections.
5.4. List of key open source components of Foreman
Foreman consists of several open source projects integrated with each other, such as the following:
- Foreman
-
Foreman is a lifecycle management application for physical and virtual systems. It helps manage hosts throughout their lifecycle, from provisioning and configuration to orchestration and monitoring.
- Katello
-
Katello is an optional plugin of Foreman that extends Foreman capabilities with additional features for content, subscription, and repository management. Katello enables Foreman to subscribe to repositories and to download content.
- Candlepin
-
Candlepin is a service for subscription management.
- Pulp
-
Pulp is a service for repository and content management.
5.5. Smart Proxy features
Smart Proxy servers provide local host management services and can mirror content from Foreman server.
To mirror content from Foreman server, Smart Proxy servers provide the following functionalities:
- Repository synchronization
-
Smart Proxy servers pull content for selected lifecycle environments from Foreman server and make this content available to the hosts they manage.
- Content delivery
-
Hosts configured to use Smart Proxy server download content from that Smart Proxy rather than from Foreman server.
- Host action delivery
-
Smart Proxy server executes scheduled actions on hosts.
- Red Hat Subscription Management (RHSM) proxy
-
Hosts are registered to their associated Smart Proxy servers rather than to the central Foreman server or the Red Hat Customer Portal.
You can use Smart Proxy to run the following services for infrastructure and host management:
- DHCP
-
Smart Proxy can manage a DHCP server, including integration with an existing solution, such as ISC DHCP servers, Active Directory, and Libvirt instances.
- DNS
-
Smart Proxy can manage a DNS server, including integration with an existing solution, such as ISC BIND and Active Directory.
- TFTP
-
Smart Proxy can integrate with any UNIX-based TFTP server.
- Realm
-
Smart Proxy can manage Kerberos realms or domains so that hosts can join them automatically during provisioning. Smart Proxy can integrate with an existing infrastructure, including FreeIPA and Active Directory.
- Puppet server
-
Smart Proxy can act as a configuration management server by running a Puppet server.
- Puppet Certificate Authority
-
Smart Proxy can integrate with the Puppet certificate authority (CA) to provide certificates to hosts.
- Baseboard Management Controller (BMC)
-
Smart Proxy can provide power management for hosts by using the Intelligent Platform Management Interface (IPMI) or Redfish standards.
- Provisioning template proxy
-
Smart Proxy can serve provisioning templates to hosts.
- OpenSCAP
-
Smart Proxy can perform security compliance scans on hosts.
- Remote Execution (REX)
-
Smart Proxy can run remote job execution on hosts.
You can configure a Smart Proxy server for a specific limited purpose by enabling only selected features on that Smart Proxy. Common configurations include the following:
- Infrastructure Smart Proxies: DNS + DHCP + TFTP
-
Smart Proxies with these services provide infrastructure services for hosts and have all necessary services for provisioning new hosts.
- Content Smart Proxies: Pulp
-
Smart Proxies with this service provide content synchronized from Foreman server to hosts.
- Configuration Smart Proxies: Pulp + Puppet + PuppetCA
-
Smart Proxies with these services provide content and run configuration services for hosts.
- Smart Proxies with DNS + DHCP + TFTP + Pulp + Puppet + PuppetCA
-
Smart Proxies with these services provide a full set of Smart Proxy features. By configuring a Smart Proxy with all these features, you can isolate hosts assigned to that Smart Proxy by providing a single point of connection for the hosts.
6. Tools for administration of Foreman
You can use multiple tools to manage Foreman.
6.1. Foreman web UI overview
You can manage and monitor your Foreman infrastructure from a browser with the Foreman web UI. Foreman supports recent versions of the Mozilla Firefox and Google Chrome browsers.
The Foreman web UI and command-line interface is translated into various languages.
6.2. Hammer CLI overview
You can configure and manage your Foreman server with CLI commands by using Hammer.
Using Hammer has the following benefits:
-
Create shell scripts based on Hammer commands for basic task automation.
-
Redirect output from Hammer to other tools.
-
Use the
--debugoption with Hammer to test responses to API calls before applying the API calls in a script. For example:hammer --debug organization list.
To issue Hammer commands, a user must have access to your Foreman server.
|
Note
|
To ensure a user-friendly and intuitive experience, the Foreman web UI takes priority when developing new functionality. Therefore, some features that are available in the Foreman web UI might not yet be available for Hammer. |
In the background, each Hammer command first establishes a binding to the API, then sends a request. This can have performance implications when executing a large number of Hammer commands in sequence. In contrast, scripts that use API commands communicate directly with the Foreman API and they establish the binding only once.
6.3. Foreman API overview
You can write custom scripts and external applications that access the Foreman API over HTTP with the Representational State Transfer (REST) API provided by Foreman server.
Using the REST API has the following benefits:
-
Configure any programming language, framework, or system with support for HTTP protocol to use the API.
-
Create client applications that require minimal knowledge of the Foreman infrastructure because users discover many details at runtime.
-
Adopt the resource-based REST model for intuitively managing a virtualization platform.
Scripts based on API commands communicate directly with the Foreman API, which makes them faster than scripts based on Hammer commands or Ansible Playbooks relying on modules within theforeman.foreman.
|
Important
|
API commands differ between versions of Foreman. When you prepare to upgrade Foreman server, update all the scripts that contain Foreman API commands. |
6.4. Remote execution in Foreman
With remote execution, you can run jobs on hosts from Smart Proxies by using shell scripts or Ansible roles and playbooks.
Use remote execution for the following benefits in Foreman:
-
Run jobs on multiple hosts at once.
-
Use variables in your commands for more granular control over the jobs you run.
-
Use host facts and parameters to populate the variable values.
-
Specify custom values for templates when you run the command.
Communication for remote execution occurs through Smart Proxy server, which means that Foreman server does not require direct access to the target host, and can scale to manage many hosts.
To use remote execution, you must define a job template. A job template is a command that you want to apply to remote hosts. You can execute a job template multiple times.
Foreman uses ERB syntax job templates. For more information, see Template writing reference in Managing hosts.
By default, Foreman includes several job templates for shell scripts and Ansible.
6.5. Automating Foreman management with Foreman Ansible Collection
Foreman Ansible Collection is a set of Ansible modules that interact with the Foreman API. You can use these modules to automate many aspects of Foreman administration.
6.6. Kickstart workflow
You can automate the installation process of a Foreman server or Smart Proxy server by creating a Kickstart file that contains all the information that is required for the installation.
When you run a Foreman Kickstart script, the script performs the following actions:
-
It specifies the installation location of a Foreman server or a Smart Proxy server.
-
It installs the predefined packages.
-
It installs Subscription Manager.
-
It uses Activation Keys to subscribe the hosts to Foreman.
-
It installs Puppet, and configures a
puppet.conffile to indicate the Foreman or Smart Proxy instance. -
It enables Puppet to run and request a certificate.
-
It runs user defined snippets.
7. Supported usage and versions of Foreman components
Foreman supports the following use cases, architectures, and versions.
7.1. Foreman operating system
You can install Foreman on the following supported operating systems.
You can run Foreman server and Smart Proxy servers on Enterprise Linux 9, Debian 12, and Ubuntu 22.04. Katello plugin packages, which provide content management capabilities, are only available for Enterprise Linux.
Foreman community only packages Foreman for x86_64.
7.2. Client operating systems
Using Foreman, you can manage multiple operating systems that have Foreman clients.
You can use Foreman to manage clients that run the following operating systems:
-
Amazon Linux
-
Debian
-
Enterprise Linux 10, 9, and 8
-
Fedora
-
OpenSUSE
-
SUSE Linux Enterprise Server
-
Ubuntu
Foreman can integrate with the following client features:
-
Ansible
-
OpenSCAP
-
OpenSSH
-
Puppet
-
Salt
-
Windows Remote Management (WinRM)
-
Operating system installers that can perform unattended installations, such as Anaconda or Debian-installer
The Katello plugin provides functionality for content and subscription management. The following utilities are provided for supported client operating systems:
-
Katello host tools
-
Subscription Manager
-
Tracer utility
8. Security considerations in Foreman
Foreman supports multiple security mechanisms to provide additional layers of protection. Implementing these security features enhances the overall security of your Foreman deployment.
|
Note
|
These security considerations apply to both Foreman server and Smart Proxy server environments. |
- Federal Information Processing Standards (FIPS) Mode
-
Foreman supports running on FIPS-enabled Red Hat Enterprise Linux hosts to comply with security standards for cryptographic modules. However, Foreman itself is not FIPS-certified. In addition, you cannot enable FIPS mode after the installation of Foreman.
FIPS mode enforces the use of validated cryptographic algorithms and modules. Enabling FIPS mode ensures that all cryptographic operations within the system adhere to strict security standards.
For more information, see Switching RHEL to FIPS mode in Red Hat Enterprise Linux 9 Security hardening.
NoteForeman supports DEFAULT and FIPS crypto-policies. The FUTURE crypto-policy is not supported for Foreman server and Smart Proxy server installations. The FUTURE policy is a stricter forward-looking security level intended for testing a possible future policy. For more information, see Using system-wide cryptographic policies in Red Hat Enterprise Linux 9 Security hardening.
- File Access Policy Daemon (
fapolicyd) -
By enabling
fapolicydon your Foreman server, you can monitor and control file and directory access, which provides an additional security layer.This feature helps prevent unauthorized code execution and enhances system integrity. You can enable or disable
fapolicydon both Foreman server and Smart Proxy server at any time, depending on your security requirements.For additional information about
fapolicyd, including instructions on enabling it, see Blocking and allowing applications by using fapolicyd in Red Hat Enterprise Linux 9 Security hardening. - Post-Quantum Cryptography (PQC)
-
Foreman community does not support PQC compatibility for Foreman.
- Security-Enhanced Linux (SELinux)
-
Foreman requires SELinux, a mandatory access control system that restricts system access and reduces the risk of security vulnerabilities. SELinux enforces policies that define which processes can access specific system resources, providing protection against unauthorized access and exploitation.
To maintain a high-security environment, Foreman community recommends running Foreman with SELinux in enforcing mode. It ensures that access control policies are strictly enforced, minimizing the risk of privilege escalation or unauthorized actions.
- Additional Security Recommendations
-
Regularly updating security policies and configurations, as well as monitoring system logs and security policies, can help detect and respond to potential threats effectively.
9. Networking considerations in Foreman
For the components of Foreman architecture to communicate, the required network ports must be open to enable incoming and outgoing traffic between the components.
9.1. Smart Proxy networking
The communication between Foreman server and hosts registered to a Smart Proxy server is routed through that Smart Proxy server. Smart Proxy server also provides Foreman services to hosts.
In a topology with hosts connecting to a Smart Proxy server, Smart Proxy server provides a single endpoint for all host network communications so that in remote network segments, only firewall ports to the Smart Proxy server itself must be open. Hosts do not need direct access to Foreman server.
In a topology with hosts connecting directly to Foreman server, hosts need direct network access to Foreman server. This applies to all Smart Proxy servers because they are hosts of Foreman server.
9.2. Foreman server port and firewall requirements
The following tables indicate the destination port and the direction of incoming and outgoing traffic for Foreman server.
| Destination Port | Protocol | Service | Source | Required For | Description |
|---|---|---|---|---|---|
53 |
TCP and UDP |
DNS |
DNS Servers and clients |
Name resolution |
DNS (optional) |
67 |
UDP |
DHCP |
Client |
Dynamic IP |
DHCP (optional) |
69 |
UDP |
TFTP |
Client |
TFTP Server (optional) |
|
443 |
TCP |
HTTPS |
Smart Proxy |
Foreman API |
Communication from Smart Proxy |
443, 80 |
TCP |
HTTPS, HTTP |
Client |
Global Registration |
Registering hosts to Foreman Port 443 is required for sending installed packages and traces, registration initiation, and uploading facts. Port 80 notifies Foreman on the |
443 |
TCP |
HTTPS |
Foreman |
Content Mirroring |
Management |
443 |
TCP |
HTTPS |
Foreman |
Smart Proxy API |
Smart Proxy functionality |
443, 80 |
TCP |
HTTPS, HTTP |
Smart Proxy |
Content Retrieval |
Content |
443, 80 |
TCP |
HTTPS, HTTP |
Client |
Content Retrieval |
Content |
1883 |
TCP |
MQTT |
Client |
Pull based REX (optional) |
Hosts for REX job notification (optional) |
4505 – 4506 |
TCP |
MQTT |
Client |
Salt (optional) |
Salt Master to Salt Minions |
5910 – 5930 |
TCP |
HTTPS |
Browsers |
Compute Resource’s virtual console |
|
8000 |
TCP |
HTTP |
Client |
Provisioning templates |
Template retrieval for client installers, iPXE or UEFI HTTP Boot |
8000 |
TCP |
HTTPS |
Client |
PXE Boot |
Installation |
8140 |
TCP |
HTTPS |
Client |
Puppet agent |
Client updates (optional) |
9090 |
TCP |
HTTPS |
Foreman |
Smart Proxy API |
Smart Proxy functionality |
9090 |
TCP |
HTTPS |
Client |
OpenSCAP |
Configure Client (if the OpenSCAP plugin is installed) |
9090 |
TCP |
HTTPS |
Discovered Node |
Discovery |
Host discovery and provisioning (if the discovery plugin is installed) |
9090 |
TCP |
HTTPS |
Client |
Pull based REX (optional) |
Hosts for REX job notification (optional) |
9191 |
TCP |
HTTPS |
Client |
Salt (optional) |
Salt API |
| Destination Port | Protocol | Service | Destination | Required For | Description |
|---|---|---|---|---|---|
ICMP |
ping |
Client |
DHCP |
Free IP checking (optional) |
|
7 |
TCP |
echo |
Client |
DHCP |
Free IP checking (optional) |
22 |
TCP |
SSH |
Target host |
Remote execution |
Run jobs |
22, 16514 |
TCP |
SSH SSH/TLS |
Compute Resource |
Foreman originated communications, for compute resources in libvirt |
|
53 |
TCP and UDP |
DNS |
DNS Servers on the internet |
DNS Server |
Resolve DNS records (optional) |
53 |
TCP and UDP |
DNS |
DNS Server |
Smart Proxy DNS |
Validation of DNS conflicts (optional) |
53 |
TCP and UDP |
DNS |
DNS Server |
Orchestration |
Validation of DNS conflicts |
68 |
UDP |
DHCP |
Client |
Dynamic IP |
DHCP (optional) |
80 |
TCP |
HTTP |
Remote repository |
Content Sync |
Remote repositories |
389, 636 |
TCP |
LDAP, LDAPS |
External LDAP Server |
LDAP |
LDAP authentication, necessary only if external authentication is enabled.
The port can be customized if |
443 |
TCP |
HTTPS |
Amazon EC2, Azure, Google Compute Engine |
Compute resources |
Virtual machine interactions (query/create/destroy) (optional) |
443 |
TCP |
HTTPS |
Smart Proxy |
Content mirroring |
Initiation |
443 |
TCP |
HTTPS |
Infoblox DHCP Server |
DHCP management |
When using Infoblox for DHCP, management of the DHCP leases (optional) |
623 |
Client |
Power management |
BMC On/Off/Cycle/Status |
||
5000 |
TCP |
HTTPS |
OpenStack Compute Resource |
Compute resources |
Virtual machine interactions (query/create/destroy) (optional) |
5900 – 5930 |
TCP |
SSL/TLS |
Hypervisor |
noVNC console |
Launch noVNC console |
5985 |
TCP |
HTTP |
Client |
WinRM |
Configure Client running Windows |
5986 |
TCP |
HTTPS |
Client |
WinRM |
Configure Client running Windows |
7911 |
TCP |
DHCP, OMAPI |
DHCP Server |
DHCP |
The DHCP target is configured using ISC and |
8443 |
TCP |
HTTPS |
Client |
Discovery |
Smart Proxy sends reboot command to the discovered host (optional) |
9090 |
TCP |
HTTPS |
Smart Proxy |
Smart Proxy API |
Management of Smart Proxies |
9.3. Smart Proxy port and firewall requirements
The following tables indicate the destination port and the direction of incoming and outgoing traffic for Smart Proxy servers.
|
Note
|
ICMP to Port 7 UDP and TCP must not be rejected, but can be dropped. The DHCP Smart Proxy sends an ECHO REQUEST to the Client network to verify that an IP address is free. A response prevents IP addresses from being allocated. |
| Destination Port | Protocol | Service | Source | Required For | Description |
|---|---|---|---|---|---|
53 |
TCP and UDP |
DNS |
DNS Servers and clients |
Name resolution |
DNS (optional) |
67 |
UDP |
DHCP |
Client |
Dynamic IP |
DHCP (optional) |
69 |
UDP |
TFTP |
Client |
TFTP Server (optional) |
|
443, 80 |
TCP |
HTTPS, HTTP |
Client |
Content Retrieval |
Content |
443, 80 |
TCP |
HTTPS, HTTP |
Client |
Content Host Registration |
Smart Proxy CA RPM installation |
443 |
TCP |
HTTPS |
Foreman |
Content Mirroring |
Management |
443 |
TCP |
HTTPS |
Foreman |
Smart Proxy API |
Smart Proxy functionality |
443 |
TCP |
HTTPS |
Client |
Content Host registration |
Initiation Uploading facts Sending installed packages and traces |
1883 |
TCP |
MQTT |
Client |
Pull based REX (optional) |
Hosts for REX job notification (optional) |
8000 |
TCP |
HTTP |
Client |
Provisioning templates |
Template retrieval for client installers, iPXE or UEFI HTTP Boot |
8000 |
TCP |
HTTP |
Client |
PXE Boot |
Installation |
8140 |
TCP |
HTTPS |
Client |
Puppet agent |
Client updates (optional) |
8443 |
TCP |
HTTPS |
Client |
Content Host registration |
Deprecated and only needed for Client hosts deployed before upgrades |
9090 |
TCP |
HTTPS |
Foreman |
Smart Proxy API |
Smart Proxy functionality |
9090 |
TCP |
HTTPS |
Client |
Register Endpoint |
Client registration with Smart Proxy servers |
9090 |
TCP |
HTTPS |
Client |
OpenSCAP |
Configure Client (if the OpenSCAP plugin is installed) |
9090 |
TCP |
HTTPS |
Discovered Node |
Discovery |
Host discovery and provisioning (if the discovery plugin is installed) |
9090 |
TCP |
HTTPS |
Client |
Pull based REX (optional) |
Hosts for REX job notification (optional) |
| Destination Port | Protocol | Service | Destination | Required For | Description |
|---|---|---|---|---|---|
ICMP |
ping |
Client |
DHCP |
Free IP checking (optional) |
|
7 |
TCP |
echo |
Client |
DHCP |
Free IP checking (optional) |
22 |
TCP |
SSH |
Target host |
Remote execution |
Run jobs |
53 |
TCP and UDP |
DNS |
DNS Servers on the internet |
DNS Server |
Resolve DNS records (optional) |
53 |
TCP and UDP |
DNS |
DNS Server |
Smart Proxy DNS |
Validation of DNS conflicts (optional) |
68 |
UDP |
DHCP |
Client |
Dynamic IP |
DHCP (optional) |
443 |
TCP |
HTTPS |
Foreman |
Smart Proxy |
Smart Proxy Configuration management Template retrieval OpenSCAP Remote Execution result upload |
443 |
TCP |
HTTPS |
Foreman |
Content |
Sync |
443 |
TCP |
HTTPS |
Foreman |
Client communication |
Forward requests from Client to Foreman |
443 |
TCP |
HTTPS |
Infoblox DHCP Server |
DHCP management |
When using Infoblox for DHCP, management of the DHCP leases (optional) |
623 |
Client |
Power management |
BMC On/Off/Cycle/Status |
||
7911 |
TCP |
DHCP, OMAPI |
DHCP Server |
DHCP |
The DHCP target is configured using ISC and |
8443 |
TCP |
HTTPS |
Client |
Discovery |
Smart Proxy sends reboot command to the discovered host (optional) |
10. Deployment path for Foreman
During installation and initial configuration of Foreman, you can customize your deployment to fit your specific needs and operational environment. By customizing each stage of the deployment process, you can choose deployment options that meet the requirements of your organization.
10.1. Installing a Foreman server
Installing an instance of Foreman server on a dedicated server is the first step to a working Foreman infrastructure.
10.1.1. Configuring Foreman server with external database
A default Foreman server installation includes installing PostgreSQL databases on the server. However, you can configure your Foreman server to use external databases instead. Moving to external databases distributes the workload and can reduce overall Foreman memory usage.
Consider using external databases if you plan to use your Foreman deployment for the following scenarios:
-
Frequent remote execution tasks. This requires a high volume of records in PostgreSQL and generates heavy database workloads.
-
High disk I/O workloads from frequent repository synchronization or content view publishing. This requires Foreman to create a record in PostgreSQL for each job.
-
High volume of hosts.
-
High volume of synchronized content.
10.2. Configuring external authentication in Foreman
The authentication methods you can configure depend on the authentication source you are using. If the native authentication features provided by Foreman are not sufficient for your use case, use this information to decide which external authentication provider best suits your requirements.
Foreman includes native support for authentication with a username and password. If you require additional methods of authentication, configure your Foreman server to use an external authentication source.
| Username and password | Single sign-on (SSO) | One-time password (OTP) | Time-based one-time password (TOTP) | PIV cards | |
|---|---|---|---|---|---|
Active Directory (direct integration) |
Yes |
Yes |
No |
No |
No |
FreeIPA |
Yes (Linux and Active Directory users) |
Yes (Linux users only) |
No |
No |
No |
Quarkus-based Keycloak |
Yes |
Yes |
Yes |
Yes |
Yes |
Wildfly-based Keycloak |
Yes |
Yes |
Yes |
Yes |
Yes |
LDAP |
Yes |
No |
No |
No |
No |
10.3. Planning organization and location context
Context in Foreman consists of organizations and locations. You can associate most resources, for example hosts, subnets, and domains, with at least one organization and location context.
Organizations and locations enable you to arrange Foreman resources into logically structured groups. For example, you can create groups based on ownership, purpose, content, or security level. You can create and manage multiple organizations through Foreman, then divide and assign subscriptions to each individual organization.
- Organizations
-
Organizations can represent different business units, departments, or teams, such as Finance, Marketing, or Web Development. To manage Red Hat content, each organization requires a separate Red Hat subscription manifest.
By creating organizations, you can create logical containers to isolate and manage their configurations separately according to their specific requirements.
- Locations
-
Locations can represent physical locations, such as countries or cities.
By creating locations, you can define geographical sites where hosts are located. For example, this is useful in environments with multiple data centers.
You can use locations to map the network infrastructure to prevent incorrect host placement or configuration. While you cannot assign a subnet, domain, or compute resources directly to a Smart Proxy server, you can assign them to a location.
Unlike organizations, locations can have a hierarchical structure. Resources and users can generally only access resources within their own context, which makes configuring organizations and locations an integral part of access management in Foreman.
Foreman server defines all locations and organizations. Each Smart Proxy server synchronizes content and handles configuration of hosts in a different location.
Your Foreman server retains the management function, while the content and configuration is synchronized between your Foreman server and Smart Proxy servers assigned to certain locations.
|
Important
|
If you use host groups to bundle provisioning and configuration information, avoid mismatching resources from mutually exclusive contexts. For example, setting a subnet from one organization or location and a compute resource from a different organization or location creates an invalid host group. |
The structure of a multi-national company includes the Finance, Marketing, and Sales departments. The company operates across United States, United Kingdom, and Japan.
The system administrator creates the following organizations on their Foreman server:
-
Finance
-
Marketing
-
Sales
Additionally, the administrator creates the following locations on their Foreman server:
-
United States
-
United Kingdom
-
Japan
The administrator can define a nested location hierarchy to divide the United States location into additional locations based on specific cities:
-
Boston
-
Phoenix
-
San Francisco
10.4. Installing Smart Proxy servers
By installing Smart Proxy servers, you extend the reach and scalability of your Foreman deployment. You register each Smart Proxy server to Foreman server and configure it to provide the required services within your Foreman deployment.
You can install a Smart Proxy server in each of your geographic locations. By assigning a Smart Proxy to each location, you decrease the load on Foreman server, increase redundancy, and reduce bandwidth usage.
|
Note
|
The maximum number of Smart Proxy servers that Foreman server can support has no fixed limit. It was tested that a Foreman server can support 17 Smart Proxy servers with 2 vCPUs. |
Decide what services you want to enable on each Smart Proxy server. You can configure the DNS, DHCP, and TFTP services on one of your Smart Proxy servers or you can use an external server to provide these services to your Smart Proxy servers.
10.5. Adding a Red Hat subscription to Foreman
A Red Hat subscription manifest is a set of encrypted files that contains your subscription information. Adding a Red Hat subscription ensures you can use Red Hat content in your Foreman deployment.
|
Note
|
If you want to manage hosts running Red Hat Enterprise Linux, import a Red Hat manifest. For more information, see Managing Red Hat subscriptions in Managing content. |
Foreman server uses information from the Red Hat subscription manifest to access the Red Hat CDN and find what repositories are available for the associated subscription.
|
Warning
|
Deleting a subscription manifest removes all the subscriptions attached to running hosts and activation keys. |
10.6. Defining your content library
To ensure that your Foreman server can manage software and provide it to your hosts, you must create repositories and synchronize them.
Your Foreman content library can include the following types of content:
- Red Hat content
-
The Red Hat subscription manifest determines what Red Hat repositories your Foreman server can access. Red Hat content is already organized into products.
For example, Red Hat Enterprise Linux Server is a product in Foreman. The repositories for the Red Hat Enterprise Linux Server product consist of different versions, architectures, and add-ons. When you enable a Red Hat repository, Foreman automatically creates an associated product.
- Oracle ULN content
-
You can use Foreman to manage hosts running Oracle Linux. For more information, see ULN repositories in Managing content.
- SUSE content
-
You can use Foreman to manage hosts running SUSE Linux Enterprise Server. For more information, see Managing SUSE content in Managing content.
- Ubuntu ESM content
-
You can use Foreman to manage hosts running Ubuntu. For more information, see Synchronizing Ubuntu Expanded Security Maintenance content in Managing content.
- Other sources of content
-
To distribute content from custom sources, you must create products and repositories manually. You can organize other content into products however you want.
For example, you can create an EPEL (Extra Packages for Enterprise Linux) product and add an "EPEL 9 x86_64" repository to it.
Creating repositories allows you to choose the specific software required for your environment. By creating only the necessary repositories, you avoid downloading unnecessary content.
Synchronizing repositories downloads the content from Red Hat CDN or another source to your Foreman server. The synchronized content is stored on your Foreman server, eliminating the need for hosts to access the repositories. You can synchronize repositories manually, or you can create a sync plan to ensure synchronization runs on a regular basis.
10.7. Defining content access strategies for hosts
When defining your content lifecycle in Foreman, you can use content views and lifecycle environments to define which hosts can access which content and content versions.
By default, Foreman includes the Default Organization View content view and the Library lifecycle environment.
- Default Organization View
-
The Default Organization View is the default content view in Foreman that contains all the content that is synchronized to Foreman. After you update your content, such as by adding or removing a repository, the update is immediately reflected in Default Organization View.
- Library
-
The Library lifecycle environment is the default lifecycle environment in Foreman. Every newly published content view version is automatically published to the Library lifecycle environment. You can also promote specific content view versions to the Library lifecycle environment if needed.
In smaller deployments or when you do not require content versioning and environment promotion, you can associate a host to the Library environment under the Default Organization View without configuring additional lifecycle environments.
10.8. Defining role-based access control policies
You can define role-based access control policies to manage access to Foreman resources. A role-based access control policy is a set of rules that defines which users can access which resources and what actions they can perform on those resources.
10.8.1. Roles in Foreman
Users in Foreman can have one or more roles assigned. These roles are associated with permissions that enable users to perform specified administrative actions in Foreman. Permission filters define the actions allowed for a certain resource type.
Foreman provides a set of predefined roles with permissions sufficient for standard tasks. You can also configure custom roles.
|
Note
|
One of the predefined roles is the Default role. Foreman assigns the Default role to every user in the system. By default, the Default role grants only a limited set of permissions. Be aware that if you add a permission to the Default role, every Foreman users will gain that permission. Assigning a different role to a user does not remove the Default role from the user. |
The following types of roles are commonly defined within various Foreman deployments:
- Roles related to applications or parts of infrastructure
-
For example, roles for owners of Enterprise Linux as the operating system as opposed to roles for owners of application servers and database servers.
- Roles related to a particular stage of the software lifecycle
-
For example, roles divided among the development, testing, and production phases, where each phase has one or more owners.
- Roles related to specific tasks
-
For example, you can create a role for security managers and a role for license managers, depending on the specific tasks users need to be able to perform within your organization.
10.8.2. Best practices for role-based access control in Foreman
When implementing role-based access control in Foreman, consider the following guidelines for optimal results.
-
Define the expected tasks and responsibilities: Define the subset of the Foreman infrastructure that you want the role to access as well as actions permitted on this subset. Think of the responsibilities of the role and how it differs from other roles.
-
Use predefined roles whenever possible: Foreman provides several sample roles that you can use. Copying and editing an existing role can be a good start for creating a custom role.
-
Adopt a granular approach to user role management: Define roles with specific and well-scoped permissions. Note that each user can have multiple roles assigned and that permissions from these roles are cumulative.
-
Add permissions gradually and test the results: When creating a custom role, start with a limited set of permissions and add permissions one by one, while testing continuously. Ensure to test your custom role to verify that it works as intended.
-
Consider areas of interest and granting read-only access: Even though a role has a limited area of responsibility, it might need a wider set of permissions. Therefore, you can grant the role a read-only access to parts of Foreman infrastructure that influence its area of responsibility.
10.9. Configuring provisioning
After your basic Foreman infrastructure is in place, you can start configuring provisioning to ensure that Foreman can seamlessly create, configure, and manage hosts.
The provisioning process depends on whether you want to provision bare-metal hosts, virtual machines, or cloud instances, but it includes defining installation media, configuring provisioning templates, and other tasks. If you are provisioning virtual machines or cloud instances, you must also integrate your compute provider with Foreman by connecting the provider as a compute resource to Foreman.
The following Foreman features support automating the provisioning of your hosts:
-
Provisioning templates enable you to define the way Foreman installs an operating system on your hosts.
-
The Discovery service enables you to detect unknown hosts and virtual machines on the provisioning network.
This requires the Discovery plugin. For more information, see Installing the Discovery service in Provisioning hosts.
-
Host groups enable you to standardize provisioning of host configurations.
10.10. Overview of recommended disaster recovery plans
Choose a disaster recovery plan that best helps ensure the continuity of Foreman services in your deployment.
- Snapshots of virtualized Foreman server
-
- How do I back up?
-
Virtualize your Foreman server and use the hypervisor tools to take virtual machine snapshots of the server. This method is suitable if you can run Foreman in a virtual machine.
- How will I recover in case of a disruptive event?
-
To recover Foreman services, restore a virtual machine snapshot.
- Disadvantages and expected impact
-
Expect some amount of data inconsistency after recovery, based on how old your last snapshot is. You will lose data changes that have occurred since the snapshot you are using to recover was taken.
- Active and passive Foreman server, with external storage
-
- How do I back up?
-
Store the following critical data on network attached storage: content in
/var/lib/pulpand database in/var/lib/pgsql. Replicate this storage into a different data center. Attach the storage to a Foreman server that is a clone of the primary Foreman server but runs passively. - How will I recover in case of a disruptive event?
-
To recover Foreman services, switch DNS records of the active Foreman server with the passive Foreman server. This ensures that the passive server becomes the active server. All hosts remain connected without configuration updates.
- Disadvantages and expected impact
-
If the network attached storage is replicated to another location, expect some amount of data inconsistency after recovery based on the synchronization interval.
- Active and passive Foreman server, with backup and restore
-
- How do I back up?
-
Ensure periodic backups of your Foreman server. Copy this backup to a passive Foreman server and restore it on the passive server.
- How will I recover in case of a disruptive event?
-
To recover Foreman services, switch DNS records of the active Foreman server with the passive Foreman server. This ensures that the passive server becomes the active server. All hosts remain connected without configuration updates.
- Disadvantages and expected impact
-
Expect some amount of data inconsistency after recovery, based on how often you took and restored backups and on how long it takes to complete the restore process.
- Dual active Foreman server
-
- How do I back up?
-
Operate an active, independent Foreman server per data center. Hosts from each data center are registered to the Foreman server in that data center. Then configure automation to ensure recovery in case of a disruptive event. For example, you can periodically run a health check and if the health check discovers that the current Foreman server a host is registered to does not resolve, the host is re-registered to the other Foreman server.
To minimize downtime, you can automate the recovery in various ways. For example, you can use the Foreman Ansible collection. For more information, see Using the Foreman Ansible Collection.
- How will I recover in case of a disruptive event?
-
To recover Foreman services, re-register all hosts to the Foreman server in the other data center.
- Disadvantages and expected impact
-
You must ensure that content synchronization and content view creation are synchronized to create the same content view in each Foreman and prevent content drift. Content drift occurs when available content deviates from the intended state defined by a content view. If you fail to prevent content drift, expect inconsistency in the content that is available to hosts.
10.11. Subscriptions tracking configuration
For successful tracking of your subscriptions usage, you have to perform the following configuration tasks.
In both connected and disconnected scenarios, perform the following task:
-
Set the system purpose for hosts in Foreman. For more information, see Editing the system purpose of a host in Managing hosts.
In the connected scenarios, also perform the following tasks:
-
If you use a hypervisor with virtual machines, configure virt-who on Foreman server. For more information, see Configuring virt-who for virtual machine subscriptions.
-
Configure inventory upload in Foreman and install the Insights client on hosts. For more information, see Monitoring hosts by using Insights in Red Hat Hybrid Cloud Console in Managing hosts.
-
Activate the Subscriptions service in the Red Hat Hybrid Cloud Console if needed. For more information, see Activating and opening the subscriptions service in Getting Started with the Subscriptions Service.
10.12. Additional deployment tasks
Foreman offers a range of additional capabilities that you can use to further enhance your Foreman deployment.
- Remote execution commands on hosts
-
With remote execution, you can perform various tasks on multiple hosts simultaneously. Foreman supports the following modes of transport for remote execution: pull-based mode (over MQTT/HTTPS) and push-based mode (over SSH).
For more information, see Configuring and setting up remote jobs in Managing hosts.
- Automating tasks with a configuration management tool
-
By integrating Foreman with a configuration management tool, you can automate repetitive tasks and ensure consistent configuration of your hosts.
You can use Ansible to configure hosts. For more information on using Ansible with Foreman, see Configuring hosts by using Ansible.
You can use Puppet to configure hosts. For more information on using Puppet with Foreman, see Configuring hosts by using Puppet.
You can use Salt to configure hosts. For more information on using Salt with Foreman, see Configuring hosts by using Salt.
- Security management with OpenSCAP
-
You can enable the OpenSCAP plugin on your Foreman server and any Smart Proxy servers. With OpenSCAP, you can manage compliance policies and run security compliance scans on your hosts. After the scan completes, a compliance report is uploaded to your Foreman server.
For more information, see Managing security compliance.
- Load balancing
-
With load balancing configured on your Smart Proxy servers, you can improve performance on Smart Proxy servers while also improving performance and stability for host connections to Foreman.
For more information, see Configuring Smart Proxies with a load balancer.
11. Common deployment scenarios
This section provides a brief overview of common deployment scenarios for Foreman. Note that many variations and combinations of the following layouts are possible.
11.1. Single location with segregated subnets
If your infrastructure requires multiple isolated networks in one geographic location, you can create segregated subnets and manage them with a single Smart Proxy.
Your infrastructure might require multiple isolated subnets even if Foreman is deployed in a single geographic location. This can be achieved for example by deploying multiple Smart Proxy servers with DHCP and DNS services, but the recommended way is to create segregated subnets using a single Smart Proxy. This Smart Proxy is then used to manage hosts and compute resources in those segregated networks to ensure they only have to access the Smart Proxy for provisioning, configuration, errata, and general management. For more information on configuring subnets, see Managing hosts.
11.2. Multiple locations
Create at least one Smart Proxy server per geographic location to save bandwidth by having hosts obtain content locally. Only your Smart Proxy server synchronizes content from remote repositories, making your provisioning infrastructure more reliable and easier to configure.
Foreman community recommends to create at least one Smart Proxy server per geographic location. This practice can save bandwidth since hosts obtain content from a local Smart Proxy server. Synchronization of content from remote repositories is done only by the Smart Proxy, not by each host in a location. In addition, this layout makes the provisioning infrastructure more reliable and easier to configure.
11.3. Content view scenarios
You can organize content views and lifecycle environments to match your workflow, from simple single-environment setups to complex application-specific paths that enable individual release cycles and testing before production deployment.
The following section provides general scenarios for deploying content views as well as lifecycle environments.
The default lifecycle environment called Library gathers content from all connected sources. It is not recommended to associate hosts directly with the Library as it prevents any testing of content before making it available to hosts. Instead, create a lifecycle environment path that suits your content workflow. The following scenarios are common:
-
A single lifecycle environment – content from Library is promoted directly to the production stage. This approach limits the complexity but still allows for testing the content within the Library before making it available to hosts.
-
A single lifecycle environment path – both operating system and applications content is promoted through the same path. The path can consist of several stages, which enables thorough testing but requires additional effort. For example, you can use the Development, QA, and Production stages.
-
Application specific lifecycle environment paths – each application has a separate path, which allows for individual application release cycles. You can associate specific compute resources with application lifecycle stages to facilitate testing. However, this scenario increases the maintenance complexity.
The following content view scenarios are common:
-
All in one content view – a content view that contains all necessary content for the majority of your hosts. Reducing the number of content views is an advantage in deployments with constrained resources (time, storage space) or with uniform host types. However, this scenario limits the content view capabilities such as time based snapshots or intelligent filtering. Any change in content sources affects a proportion of hosts.
-
Host specific content view – a dedicated content view for each host type. This approach can be useful in deployments with a small number of host types (up to 30). However, it prevents sharing content across host types as well as separation based on criteria other than the host type, for example, between operating system and applications. With critical updates every content view has to be updated, which increases maintenance efforts.
-
Host specific composite content view – a dedicated combination of content views for each host type. This approach enables separating host specific and shared content, for example you can have dedicated content views for the operating system and application content. By using a composite, you can manage your operating system and applications separately and at different frequencies.
-
Component based content view – a dedicated content view for a specific application. For example a database content view can be included into several composite content views. This approach allows for greater standardization but it leads to an increased number of content views.
The optimal solution depends on the nature of your host environment. Avoid creating a large number of content views, but keep in mind that the size of a content view affects the speed of related operations (publishing, promoting). Also make sure that when creating a subset of packages for the content view, all dependencies are included as well. Note that Kickstart repositories should not be added to content views, as they are used for host provisioning only.
11.4. Foreman server with multiple manifests
You can use many Red Hat Network subscription manifests in one Foreman server to manage systems from different Red Hat Network accounts or entities. This allows you to assign subscriptions to separate organizations and manage those organizations independently.
If you plan to have more than one Red Hat Network account, or if you want to manage systems belonging to another entity that is also a Red Hat Network account holder, then you and the other account holder can assign subscriptions, as required, to manifests. A customer that does not have a Foreman subscription can create a Subscription Asset Manager manifest, which can be used with Foreman, if they have other valid subscriptions. You can then use the multiple manifests in one Foreman server to manage multiple organizations.
The following diagram shows two Red Hat Network account holders, who want their systems to be managed by the same Foreman installation. In this scenario, Example Corporation 1 can allocate any subset of their 60 subscriptions, in this example they have allocated 30, to a manifest. This can be imported into the Foreman as a distinct Organization. This allows system administrators the ability to manage Example Corporation 1’s systems using Foreman completely independently of Example Corporation 2’s organizations (R&D, Operations, and Engineering).
When creating a Red Hat subscription manifest:
-
Add the subscription for Foreman server to the manifest if planning a disconnected or self-registered Foreman server. This is not necessary for a connected Foreman server that is subscribed using the Subscription Manager utility on the base system.
-
Add subscriptions for all Smart Proxy servers you want to create.
-
Add subscriptions for all Red Hat products you want to manage with Foreman.
-
Note the date when the subscriptions are due to expire and plan for their renewal before the expiry date.
-
Create one manifest per organization. You can use multiple manifests and they can be from different Red Hat subscriptions.
Foreman allows the use of future-dated subscriptions in the manifest. This enables uninterrupted access to repositories when future-dated subscriptions are added to a manifest before the expiry date of existing subscriptions.
Note that the Red Hat subscription manifest can be modified and reloaded to Foreman server in case of any changes in your infrastructure, or when adding more subscriptions. Manifests should not be deleted. If you delete the manifest from the Red Hat Customer Portal or in the Foreman web UI it will unregister all of your hosts.
11.5. Host group structures
You can organize host groups by using flat, lifecycle environment-based, application-based, or location-based structures to simplify maintenance of host settings and match your workflow. Nested groups inherit parameters from parent groups.
The fact that host groups can be nested to inherit parameters from each other allows for designing host group hierarchies that fit particular workflows. A well planned host group structure can help to simplify the maintenance of host settings. This section outlines four approaches to organizing host groups.
- Flat structure
-
The advantage of a flat structure is limited complexity, as inheritance is avoided. In a deployment with few host types, this scenario is the best option. However, without inheritance there is a risk of high duplication of settings between host groups.
- Lifecycle environment based structure
-
In this hierarchy, the first host group level is reserved for parameters specific to a lifecycle environment. The second level contains operating system related definitions, and the third level contains application specific settings. Such structure is useful in scenarios where responsibilities are divided among lifecycle environments. For example, if there is a dedicated owner for the Development, QA, and Production lifecycle stages.
- Application based structure
-
This hierarchy is based on roles of hosts in a specific application. For example, it enables defining network settings for groups of back-end and front-end servers. The selected characteristics of hosts are segregated, which supports Puppet-focused management of complex configurations. However, the content views can only be assigned to host groups at the bottom level of this hierarchy.
- Location based structure
-
In this hierarchy, the distribution of locations is aligned with the host group structure. In a scenario where the location or Smart Proxy server topology determines many other attributes, this approach is the best option. However, this structure complicates sharing parameters across locations, therefore in complex environments with a large number of applications, the number of host group changes required for each configuration change increases significantly.
11.6. Inter-Server Synchronization scenarios
You can use Inter-Server Synchronization to synchronize content between Foreman servers, including air-gapped servers. In these scenarios, you copy selected content views or all Library content from an upstream server to downstream servers over a network or through physical export.
Foreman uses Inter-Server Synchronization (ISS) to synchronize content between two Foreman servers including those that are air gapped.
You can use ISS in cases such as:
-
If you want to copy some but not all content from your Foreman server to other Foreman servers. For example, you have content views that your IT department consumes from Foreman server, and you want to copy content from those content views to other Foreman servers.
-
If you want to copy all Library content from your Foreman server to other Foreman servers. For example, you have products and repositories that your IT department consumes from Foreman server in the Library, and you want to copy all products and repositories in that organization to other Foreman servers.
|
Note
|
You cannot use ISS to synchronize content from Foreman server to Smart Proxy server. Smart Proxy server supports synchronization natively. For more information, see Smart Proxy server Overview in Planning for Foreman. |
There are different ways of using ISS. The way you can use depends on your multi-server setup that can fall to one of the following scenarios.
In a disconnected scenario, there is the following setup:
-
The upstream Foreman server is connected to the internet. This server consumes content from the Red Hat Content Delivery Network (CDN) or custom sources.
-
The downstream Foreman server is completely isolated from all external networks.
-
The downstream Foreman server can communicate with a connected upstream Foreman server over an internal network.
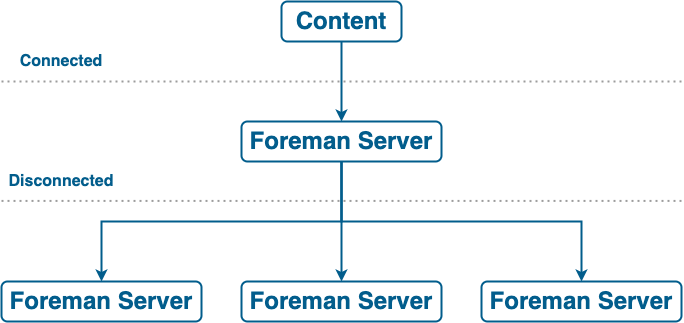
You can configure your downstream Foreman server to synchronize content from the upstream Foreman server over the network.
In an air-gapped scenario, there is the following setup:
-
The upstream Foreman server is connected to the internet. This server consumes content from the Red Hat CDN or custom sources.
-
The downstream Foreman server is completely isolated from all external networks.
-
The downstream Foreman server does not have a network connection to a connected upstream Foreman server.
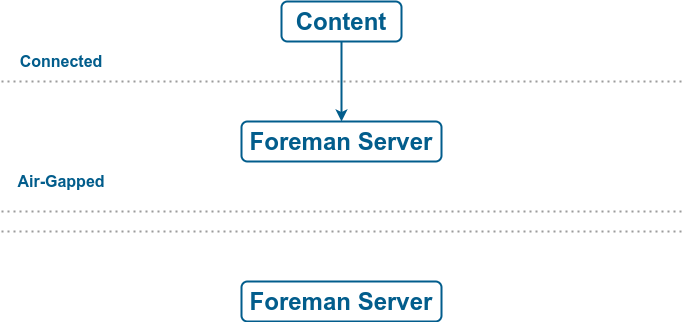
The only way for an air-gapped downstream Foreman server to receive content updates is by exporting payload from the upstream Foreman server, bringing it physically to the downstream Foreman server, and importing the payload. For more information, see Synchronizing Content Between Foreman servers in Managing content.
You can configure your downstream Foreman server to synchronize content by using exports.
11.7. Deploying Foreman on AWS
You can deploy Foreman server, Smart Proxy servers, and hosts in Amazon Web Services (AWS) using various configurations. Options range from simple single-region setups to multi-region deployments with VPN connections or direct connections between on-premises and cloud environments.
You can run Foreman server, Smart Proxy servers, and hosts in your Amazon Web Services (AWS) environment. You can deploy Foreman on Amazon Web Services (AWS) in several scenarios.
- One-region setup
-
This is the least complex configuration of Foreman in AWS. Deploy both Foreman server and the hosts residing within the same region and within the Virtual Private Cloud (VPC) You can also use a different availability zone.
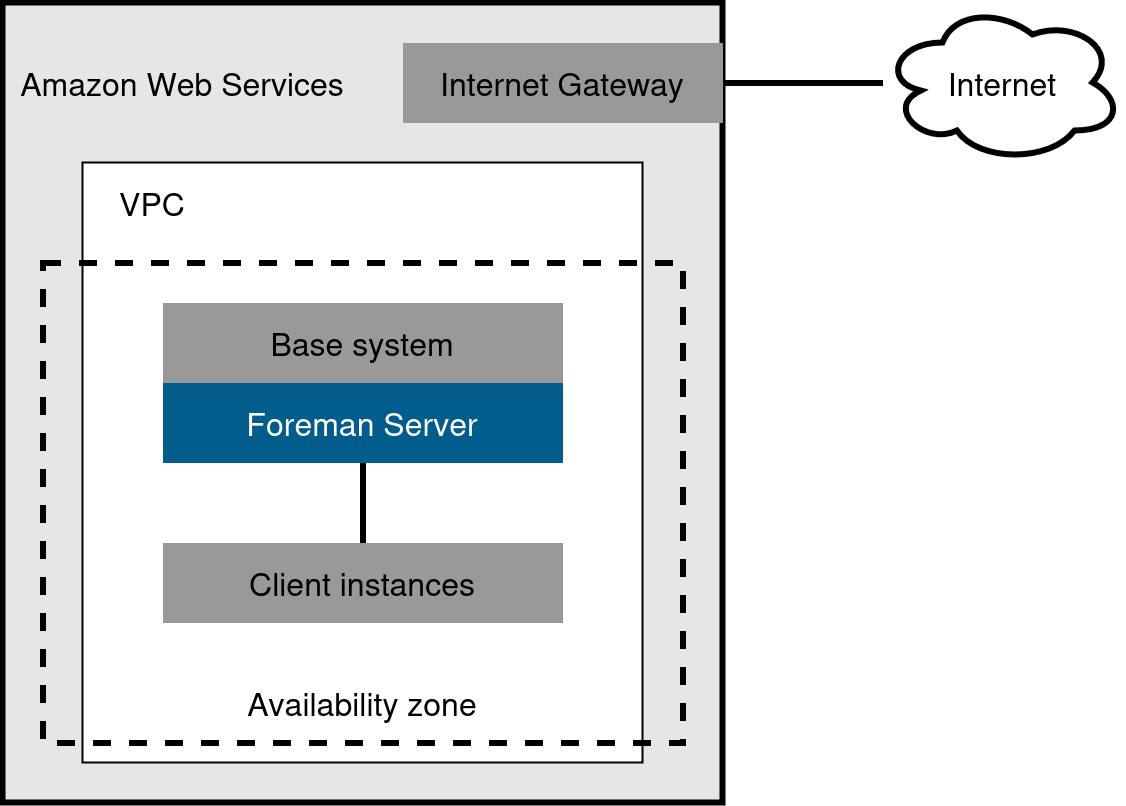 Figure 7. One-region setup
Figure 7. One-region setup - Connecting on-premises and AWS region
-
Create a VPN connection between the on-premises location and the AWS region where your Smart Proxy server is located. It is also possible to use the external host name of Foreman server when you register the instance that runs Smart Proxy.
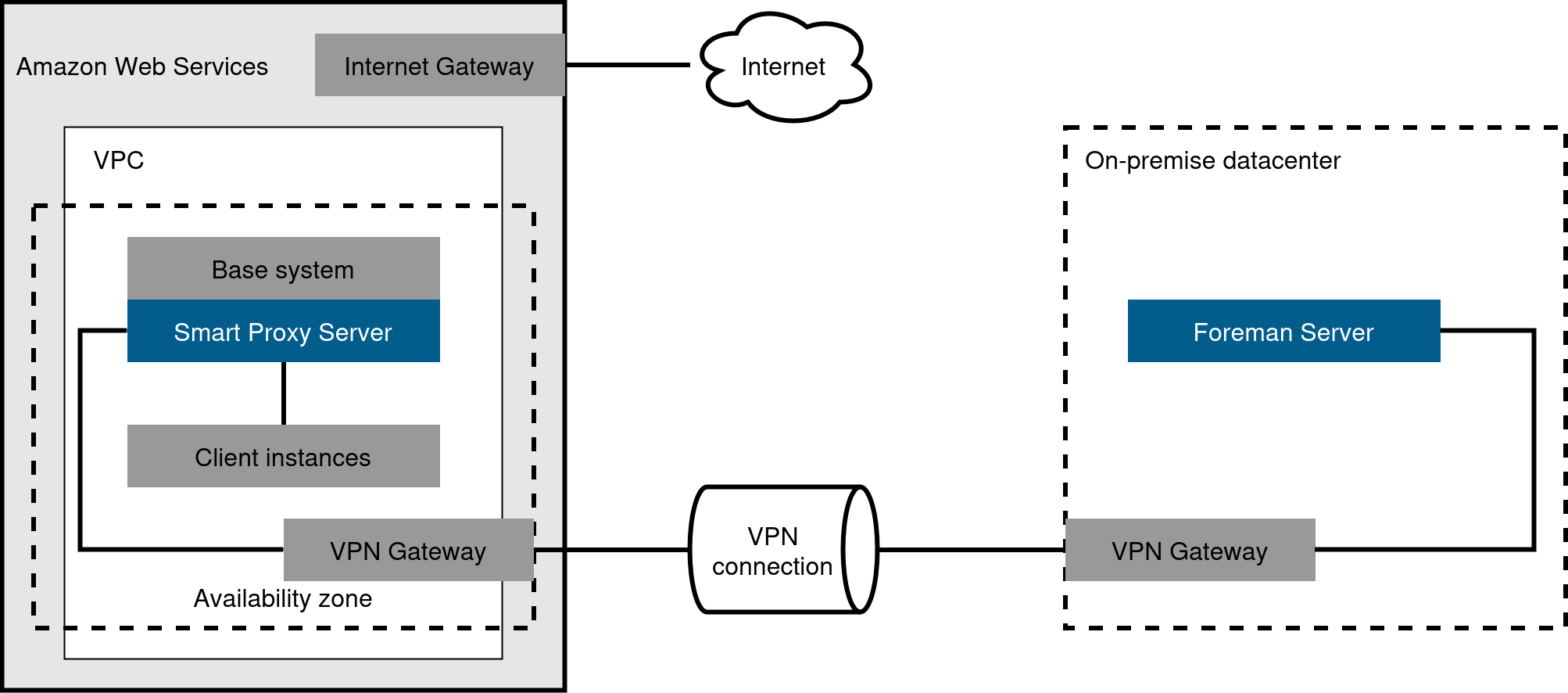 Figure 8. Site-to-site VPN connection between the AWS region and the on-premises data center
Figure 8. Site-to-site VPN connection between the AWS region and the on-premises data center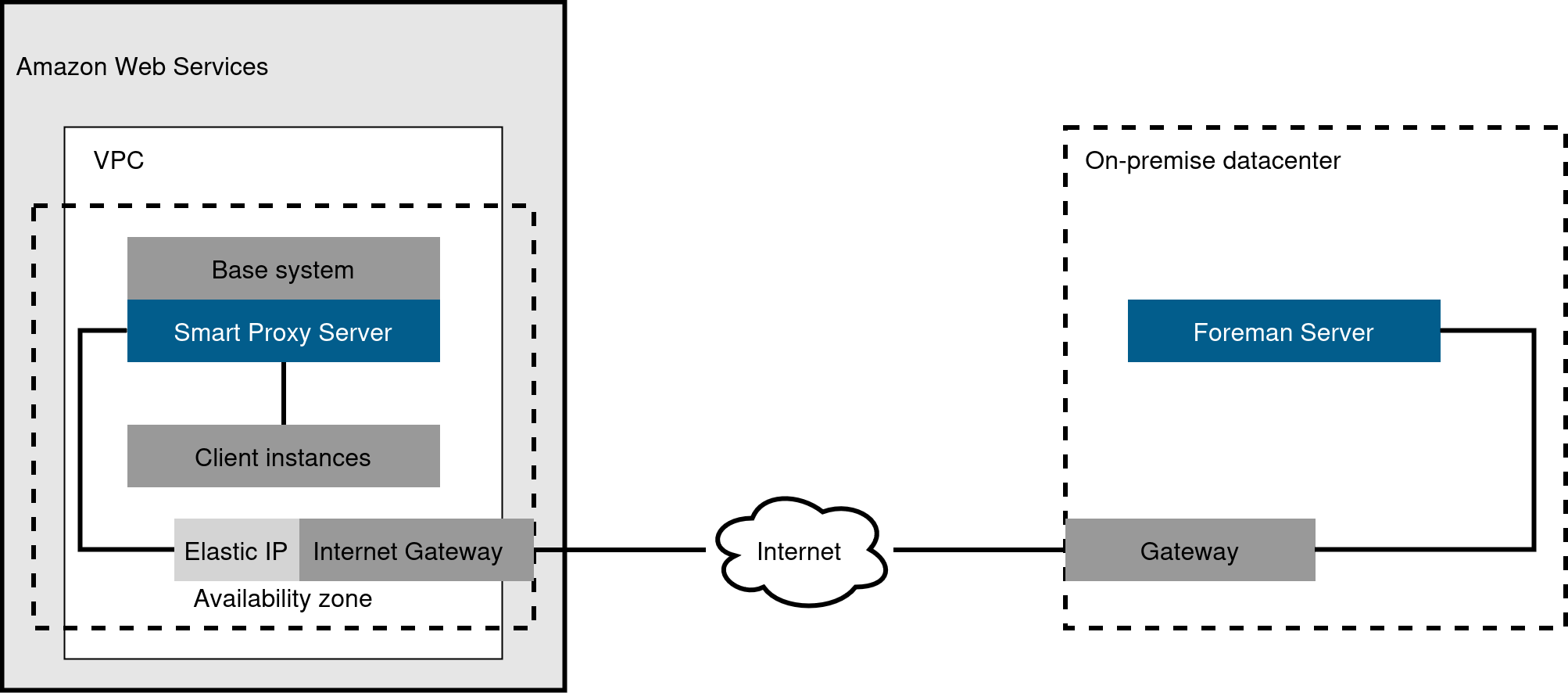 Figure 9. Direct connection using the external DNS host name
Figure 9. Direct connection using the external DNS host name - Connecting different regions
-
Create a site-to-site VPN connection between different regions so that you can use the internal DNS host name when you register the instance that runs Smart Proxy to Foreman server. If you do not establish a site-to-site VPN connection, use the external DNS host name when you register the instance that runs Smart Proxy to Foreman server.
NoteMost public cloud providers do not charge for data being transferred into a region or between availability zones within a single region. However, they charge for data leaving the region to the internet.
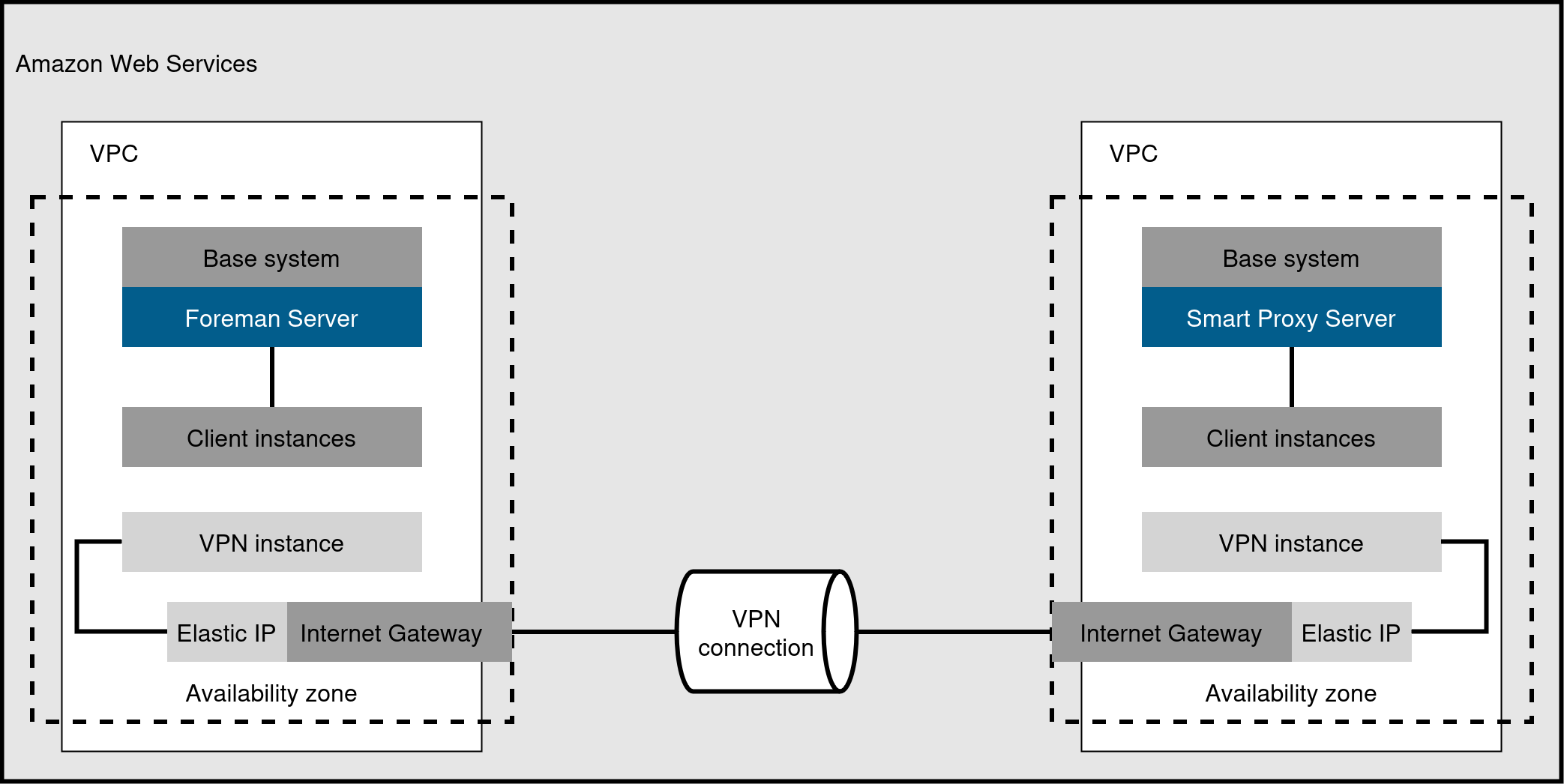 Figure 10. Site-to-site VPN connection between AWS regions
Figure 10. Site-to-site VPN connection between AWS regions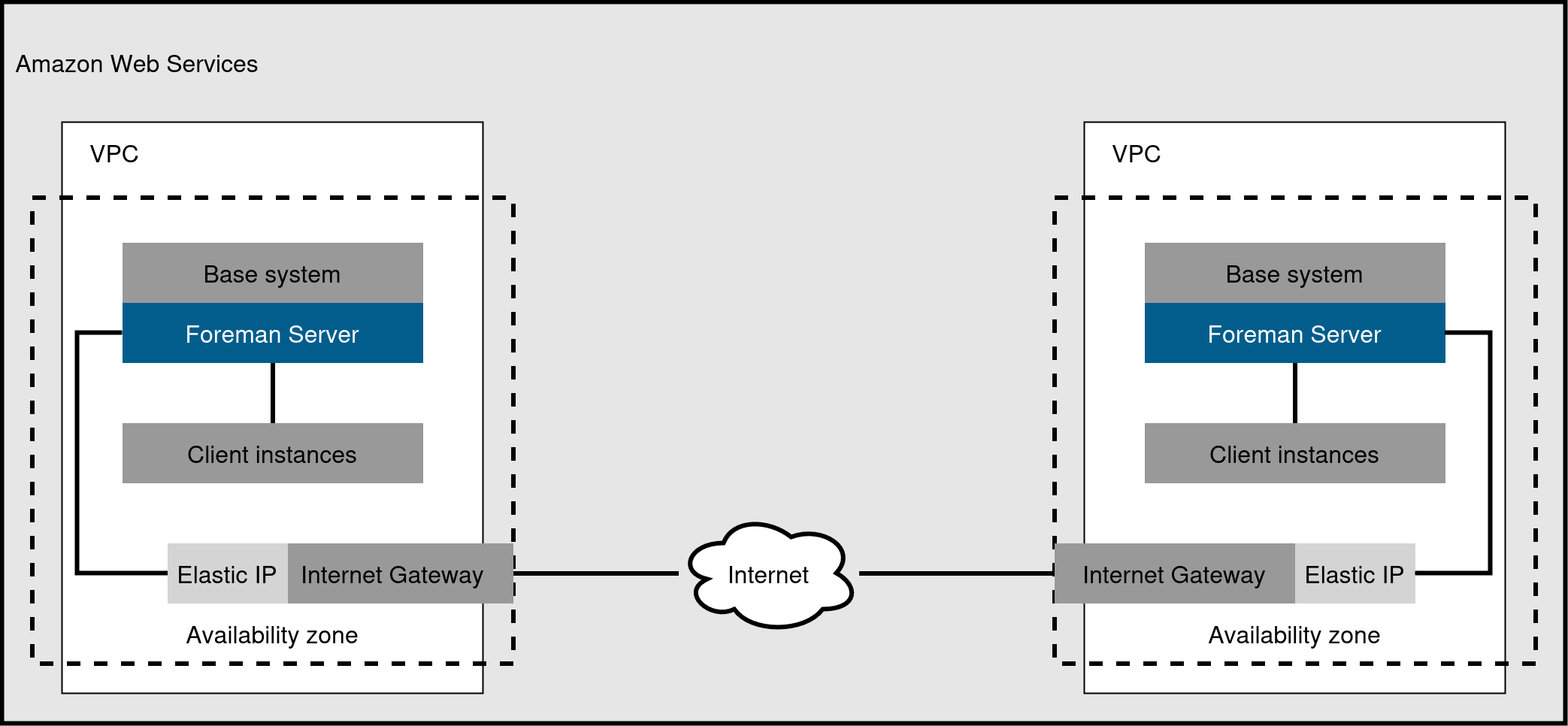 Figure 11. Direct connection using the external DNS host name
Figure 11. Direct connection using the external DNS host name
12. Provisioning requirements in Foreman
An important feature of Foreman is unattended provisioning of hosts. To achieve this, Foreman uses DNS and DHCP infrastructures, PXE booting, TFTP, and Kickstart. Use this chapter to understand the working principle of these concepts.
12.1. PXE booting in Foreman
Preboot execution environment (PXE) provides the ability to boot a system over a network. Instead of using local hard drives or a CD-ROM, PXE uses DHCP to provide host with standard information about the network, to discover a TFTP server, and to download a boot image.
- PXE sequence
-
-
The host boots the PXE image if no other bootable image is found.
-
A NIC of the host sends a broadcast request to the DHCP server.
-
The DHCP server receives the request and sends standard information about the network: IP address, subnet mask, gateway, DNS, the location of a TFTP server, and a boot image.
-
The host obtains the boot loader
image/pxelinux.0and the configuration filepxelinux.cfg/00:MA:CA:AD:Dfrom the TFTP server. -
The host configuration specifies the location of a kernel image,
initrdand Kickstart. -
The host downloads the files and installs the image.
-
- PXE booting requirements
-
-
Network requirements:
-
Optional: If the host and the DHCP server are separated by a router, configure the DHCP relay agent and point to the DHCP server.
-
-
Client requirements:
-
Ensure that all the network-based firewalls are configured to allow clients on the subnet to access the Smart Proxy. For more information, see Networking considerations in Foreman.
-
Ensure that your client has access to the DHCP and TFTP servers.
-
-
Foreman requirements:
-
Ensure that both Foreman server and Smart Proxy have DNS configured and are able to resolve provisioned host names.
-
Ensure that the UDP ports 67 and 68 are accessible by the client to enable the client to receive a DHCP offer with the boot options.
-
Ensure that the UDP port 69 is accessible by the client so that the client can access the TFTP server on the Smart Proxy.
-
Ensure that the TCP port 80 is accessible by the client to allow the client to download files and Kickstart templates from the Smart Proxy.
-
Ensure that the host provisioning interface subnet has a DHCP Smart Proxy set.
-
Ensure that the host provisioning interface subnet has a TFTP Smart Proxy set.
-
Ensure that the host provisioning interface subnet has a Templates Smart Proxy set.
-
Ensure that DHCP with the correct subnet is enabled using the Foreman installer.
-
Enable TFTP using the Foreman installer.
-
-
12.2. HTTP booting in Foreman
You can use HTTP booting to boot systems over a network using HTTP.
- HTTP booting requirements with managed DHCP
-
-
Client requirements:
-
All the network-based firewalls are configured to allow clients on the subnet to access the Smart Proxy. For more information, see Networking considerations in Foreman.
-
Your client has access to the DHCP and DNS servers.
-
Your client has access to the HTTP UEFI Boot Smart Proxy.
-
-
Network requirements:
-
Optional: If the host and the DHCP server are separated by a router, configure the DHCP relay agent and point to the DHCP server.
-
-
Foreman requirements:
NoteAlthough TFTP protocol is not used for HTTP UEFI Booting, Foreman uses TFTP Smart Proxy API to deploy boot loader configuration.
-
Both Foreman server and Smart Proxy have DNS configured and are able to resolve provisioned host names.
-
The UDP ports 67 and 68 are accessible by the client so that the client can send and receive a DHCP request and offer.
-
Ensure that the TCP port 8000 is open for the client to download the boot loader and Kickstart templates from the Smart Proxy.
-
The TCP port 9090 is open for the client to download the boot loader from the Smart Proxy using the HTTPS protocol.
-
The subnet that functions as the host’s provisioning interface has a DHCP Smart Proxy, an HTTP Boot Smart Proxy, a TFTP Smart Proxy, and a Templates Smart Proxy
-
-
- HTTP booting requirements with unmanaged DHCP
-
-
Client requirements:
-
HTTP UEFI Boot URL must be set to one of:
-
http://smartproxy.example.com:8000 -
https://smartproxy.example.com:9090
-
-
Ensure that your client has access to the DHCP and DNS servers.
-
Ensure that your client has access to the HTTP UEFI Boot Smart Proxy.
-
Ensure that all the network-based firewalls are configured to allow clients on the subnet to access the Smart Proxy. For more information, see Networking considerations in Foreman.
-
-
Network requirements:
-
An unmanaged DHCP server available for clients.
-
An unmanaged DNS server available for clients. In case DNS is not available, use IP address to configure clients.
-
-
Foreman requirements:
NoteAlthough TFTP protocol is not used for HTTP UEFI Booting, Foreman use TFTP Smart Proxy API to deploy boot loader configuration.
-
Ensure that both Foreman server and Smart Proxy have DNS configured and are able to resolve provisioned host names.
-
Ensure that the UDP ports 67 and 68 are accessible by the client so that the client can send and receive a DHCP request and offer.
-
Ensure that the TCP port 8000 is open for the client to download boot loader and Kickstart templates from the Smart Proxy.
-
Ensure that the TCP port 9090 is open for the client to download the boot loader from the Smart Proxy through HTTPS.
-
Ensure that the host provisioning interface subnet has an HTTP Boot Smart Proxy set.
-
Ensure that the host provisioning interface subnet has a TFTP Smart Proxy set.
-
Ensure that the host provisioning interface subnet has a Templates Smart Proxy set.
-
-
12.3. Secure Boot in Foreman
You can configure Secure Boot to ensure hosts boot with signed boot loaders.
When Foreman is installed on Enterprise Linux using foreman-installer, grub2 and shim boot loaders that are signed by Red Hat are deployed into the TFTP and HTTP UEFI Boot directory.
PXE loader options named "SecureBoot" configure hosts to load shim.efi.
On Debian and Ubuntu operating systems, the grub2 boot loader is created using the grub2-mkimage unsigned.
To perform the Secure Boot, the boot loader must be manually signed and key enrolled into the EFI firmware.
Alternatively, grub2 from Ubuntu or Enterprise Linux can be copied to perform booting.
Grub2 in Enterprise Linux 8.0-8.3 were updated to mitigate Boot Hole Vulnerability and keys of existing Enterprise Linux kernels were invalidated. To boot any of the affected Enterprise Linux kernel (or operating system installer), you must enroll keys manually into the EFI firmware for each host:
# pesign -P -h -i /boot/vmlinuz-<version> # mokutil --import-hash <hash value returned from pesign> # reboot
Appendix A: Technical users provided and required by Foreman
The Foreman installation process automatically creates system accounts. They manage files and process ownership of the components integrated into Foreman. The following table lists all the accounts created by Foreman during installation.
Some of these accounts have fixed UIDs and GIDs, while others take the next available UID and GID on the system instead. To control the UIDs and GIDs assigned to accounts, you can define accounts before installing Foreman. Because some of the accounts have hard-coded UIDs and GIDs, it is not possible to do this with all accounts created during Foreman installation.
You can predefine accounts that have Yes in the Flexible UID and GID column with custom UID and GID before installing Foreman.
Do not change the home and shell directories of system accounts because they are requirements for Foreman.
Because of potential conflicts with local users that Foreman creates, you cannot use external identity providers for the system users of the Foreman base operating system.
| User name | UID | Group name | GID | Flexible UID and GID | Home | Shell |
|---|---|---|---|---|---|---|
foreman |
N/A |
foreman |
N/A |
yes |
/usr/share/foreman |
/sbin/nologin |
foreman-proxy |
N/A |
foreman-proxy |
N/A |
yes |
/usr/share/foreman-proxy |
/sbin/nologin |
apache |
48 |
apache |
48 |
no |
/usr/share/httpd |
/sbin/nologin |
postgres |
26 |
postgres |
26 |
no |
/var/lib/pgsql |
/bin/bash |
pulp |
N/A |
pulp |
N/A |
no |
N/A |
/sbin/nologin |
puppet |
52 |
puppet |
52 |
no |
/opt/puppetlabs/server/data/puppetserver |
/sbin/nologin |
saslauth |
N/A |
saslauth |
76 |
no |
/run/saslauthd |
/sbin/nologin |
tomcat |
53 |
tomcat |
53 |
no |
/usr/share/tomcat |
/bin/nologin |
unbound |
N/A |
unbound |
N/A |
yes |
/etc/unbound |
/sbin/nologin |
Appendix B: Glossary of terms used in Foreman
This alphabetically ordered glossary provides an overview of Foreman related technical terms.
- Activation key
-
Activation keys are used by Subscription Manager to register hosts to Foreman. They define content view and lifecycle environment associations, content overrides, system purpose attributes, and other parameters to be associated with a newly created host.
They are associated to exactly one lifecycle environment and exactly one content view, though this may be a composite content view. You can use them on multiple machines and they behave like configuration information rather than traditional software license keys. You can also use multiple activation keys with a single host. When you register a host using an activation key, certain content from Foreman is provided to the host. The content that is made available depends on the content in the activation key’s content view and lifecycle environment, any content overrides present, any repository-level restrictions such as operating system or architecture, and system purpose attributes such as release version.
- Ansible
-
Ansible is an agentless open-source automation engine. For hosts running Linux, Ansible uses SSH to connect to hosts. For hosts running Microsoft Windows, Ansible relies on WinRM. It uses playbooks and roles to describe and bundle tasks. Within Foreman, you can use Ansible to configure hosts and perform remote execution.
For more information about using Ansible to configure hosts, see Configuring hosts by using Ansible. For more information about automating Foreman using Ansible, see Using the Foreman Ansible Collection.
- Answer file
-
A configuration file that defines settings for an installation scenario. Answer files are defined in the YAML format and stored in the
/etc/foreman-installer/scenarios.d/directory. To see the default values for installation scenario parameters, use theforeman-installer --full-helpcommand on your Foreman server.
- ARF report
-
Asset Reporting Format (ARF) reports are the result of OpenSCAP compliance scans on hosts which have a policy assigned. Summarizes the security compliance of hosts managed by Foreman. They list compliance criteria and whether the scanned host has passed or failed.
- Audits
-
Provide a report on changes made by a specific user. Audits can be viewed in the Foreman web UI under Monitor > Audits.
- Baseboard management controller (BMC)
-
Enables remote power management of bare-metal hosts. In Foreman, you can create a BMC interface to manage selected hosts.
- Boot disk
-
An ISO image used for PXE-less provisioning. This ISO enables the host to connect to Foreman server, boot the installation media, and install the operating system. There are several kinds of boot disks: host image, full host image, generic image, and subnet image.
- Catalog
-
A document that describes the desired system state for one specific host managed by Puppet. It lists all of the resources that need to be managed, as well as any dependencies between those resources. Catalogs are compiled by a Puppet server from Puppet Manifests and data from Puppet agents.
- Candlepin
-
A service within Katello responsible for subscription management.
- Compliance policy
-
Compliance policies refer to the application of SCAP content to hosts by using Foreman with its OpenSCAP plugin. You can create compliance policies by using the Foreman web UI, Hammer CLI, or API. A compliance policy requires the setting of a specific XCCDF profile from a SCAP content, optionally using a tailoring file. You can set up scheduled tasks on Foreman that check your hosts for compliance against SCAP content. When a compliance policy scan completes, the host sends an ARF report to Foreman.
- Compute profile
-
Specifies default attributes for new virtual machines on a compute resource.
- Compute resource
-
A compute resource is an external virtualization or cloud infrastructure that you can attach to Foreman. Foreman can provision, configure, and manage hosts within attached compute resources. Examples of compute resources include VMware or libvirt and cloud providers such as Microsoft Azure or Amazon EC2.
- Configuration Management
-
Configuration management describes the task of configuring and maintaining hosts. In Foreman, you can use Ansible, Puppet, and Salt to configure and maintain hosts with Foreman as a single source of infrastructure truth.
- Container (Docker container)
-
An isolated application sandbox that contains all runtime dependencies required by an application. Foreman supports container provisioning on a dedicated compute resource.
- Container image
-
A static snapshot of the container’s configuration. Foreman supports various methods of importing container images as well as distributing images to hosts through content views.
- Content
-
A general term for everything Foreman distributes to hosts. Content includes software packages such as
.rpmpackages, errata, or Docker images. Content is synchronized into the Library and then promoted into lifecycle environments using content views so that they can be consumed by hosts.
- Content delivery network (CDN)
-
The mechanism used to deliver Red Hat content to Foreman server.
- Content view
-
Content views are named and versioned collections of repositories. When you publish a content view, Foreman creates a new content view version. This content view version is a frozen snapshot of the current state of the repositories within the content view. Any subsequent changes to the underlying repositories will no longer affect the published content view version. Once a content view is published, it can be promoted through the lifecycle environment path, or modified using incremental upgrades.
- Composite content view
-
Composite content views contain content views, which allows for a more modular approach to manage and version content. You can choose which version of each content view is used in a composite content view.
- Discovered host
-
A bare-metal host detected on the provisioning network by the Discovery plugin.
- Discovery image
-
Refers to the minimal operating system based on Enterprise Linux that is PXE-booted on hosts to acquire initial hardware information and to communicate with Foreman server before starting the provisioning process.
- Discovery plugin
-
Enables automatic bare-metal discovery of unknown hosts on the provisioning network. The plugin consists of three components: services running on Foreman server and Smart Proxy server, and the Discovery image running on host.
- Discovery rule
-
A set of predefined provisioning rules which assigns a host group to discovered hosts and triggers provisioning automatically.
- Docker tag
-
A mark used to differentiate container images, typically by the version of the application stored in the image. In the Foreman web UI, you can filter images by tag under Content > Docker Tags.
- Enterprise Linux
-
An umbrella term for the following Red Hat Enterprise Linux-like operating systems:
-
AlmaLinux
-
CentOS Linux
-
CentOS Stream
-
Oracle Linux
-
Red Hat Enterprise Linux
-
Rocky Linux
Foreman is tested on AlmaLinux and CentOS Stream.
-
- ERB
-
Embedded Ruby (ERB) is a template syntax used in provisioning and job templates.
- Errata
-
Updated packages containing security fixes, bug fixes, and enhancements. In relationship to a host, erratum is applicable if it updates a package installed on the host and installable if it is present in the host’s content view (which means it is accessible for installation on the host).
- External node classifier (ENC)
-
A construct that provides additional data for a server to use when configuring hosts. When Puppet obtains information about nodes from an external source instead of its own database, the external source is called External node classifier. If the Puppet plugin is installed, Foreman can act as an External node classifier to Puppet servers in a Foreman deployment.
- Facter
-
A program that provides information (facts) about the system on which it is run; for example, Facter can report total memory, operating system version, architecture, and more. Puppet modules enable specific configurations based on host data gathered by Facter.
- Facts
-
Host parameters such as total memory, operating system version, or architecture. Facts are reported by Facter and used by Puppet.
- Foreman
-
Foreman is an open-source component to provision and manage hosts.
- Full host image
-
A boot disk used for PXE-less provisioning of a specific host. The full host image contains an embedded Linux kernel and init RAM disk of the associated operating system installer.
- Generic image
-
A boot disk for PXE-less provisioning that is not tied to a specific host. The generic image sends the MAC address of your host to Foreman server, which matches it against the host entry.
- Hammer
-
Hammer is a command-line interface tool for Foreman. You can execute Hammer commands from the command line or utilize it in scripts. You can use Hammer to automate certain recurring tasks as an alternative to Foreman Ansible collection or Foreman API.
- Host
-
A host is a physical, virtual, or cloud instance registered to Foreman.
- Host collection
-
A user defined group of one or more Hosts used for bulk actions such as errata installation.
- Host group
-
A host group is a template to build hosts that holds shared parameters, such as subnet or lifecycle environment. It helps to unify configuration management in Ansible, Puppet, and Salt by grouping hosts. You can nest host groups to create a hierarchical structure. For more information, see Working with host groups in Managing hosts.
- Host image
-
A boot disk used for PXE-less provisioning of a specific host. The host image only contains the boot files necessary to access the installation media on Foreman server.
- Incremental upgrade (of a content view)
-
The act of creating a new (minor) content view version in a lifecycle environment. Incremental upgrades provide a way to make in-place modification of an already published content view. Useful for rapid updates, for example when applying security errata.
- Installation Media
-
Installation media are sets of installation files used to install the base operating system during the provisioning process. An installation medium in Foreman represents the installation files for one or more operating systems, which must be accessible over the network, either through an URL or an NFS server location. It is usually either a mirror or a CD or DVD image.
Every operating system depends on exactly one path of an installation medium, whereas installation media paths may serve different operating systems at the same time. You can use operating system parameters such as
$version,$major, and$minorto parameterize the URL.
- Job
-
A command executed remotely on a host from Foreman server. Every job is defined in a job template.
- Katello
-
Katello is an open-source plugin to perform content management and subscription handling. It depends on Pulp for content management, which fetches software from repositories and stores various versions of it. It also depends on Candlepin for host registration and managing subscription manifests.
- Lazy sync
-
The ability to change the default download policy of a repository from Immediate to On Demand. The On Demand setting saves storage space and synchronization time by only downloading the packages when requested by a host.
- Location
-
A collection of default settings that represent a physical place. Location is a tag mostly used for geographical separation of hosts within Foreman. Examples include different cities or different data centers.
- Library
-
A container for content from all synchronized repositories on Foreman server. Libraries exist by default for each organization as the root of every lifecycle environment path and the source of content for every content view.
- Lifecycle environment
-
A lifecycle environment represents a step in the lifecycle environment path. It defines the stage in which certain versions of content are available to hosts, such as development, testing, and production. This way, new versions of software can be developed and tested before being deployed in a production environment, thus reducing the risk of disruption by prematurely rolled out updates. Content moves through lifecycle environments by publishing and promoting content views.
- Lifecycle environment path
-
A sequence of lifecycle environments through which content views are promoted. You can promote a content view through a typical promotion path, for example, from development to test to production. All lifecycle environment paths originate from the Library environment, which is always present by default.
- Manifest (Red Hat subscription manifest)
-
A mechanism for transferring subscriptions from the Red Hat Customer Portal to Foreman. Do not confuse with Puppet manifest.
- Migrating Foreman
-
The process of moving an existing Foreman installation to a new instance.
- OpenSCAP
-
A project implementing security compliance auditing according to the Security Content Automation Protocol (SCAP). OpenSCAP is integrated in Foreman to provide compliance auditing for hosts.
- Organization
-
An isolated collection of systems, content, and other functionality within Foreman. Organization is a tag used for organizational separation of hosts within Foreman. Examples include different teams or business units.
- Parameter
-
Defines the behavior of Foreman components during provisioning. Depending on the parameter scope, we distinguish between global, domain, host group, and host parameters. Depending on the parameter complexity, we distinguish between simple parameters (key-value pair) and smart parameters (conditional arguments, validation, overrides).
- Parametrized class (smart class parameter)
-
A parameter created by importing a class from Puppet server.
- Patch and release management
-
Patch and release management describes the process of acquiring, managing, and installing patches and software updates to your infrastructure. Using Foreman, you can keep control of the package versions available to your hosts and deliver applicable errata.
- Permission
-
Defines an action related to a selected part of Foreman infrastructure (resource type). Each resource type is associated with a set of permissions, for example the Architecture resource type has the following permissions: view_architectures, create_architectures, edit_architectures, and destroy_architectures. You can group permissions into roles and associate them with users or user groups.
- Product
-
Products are named collections of one or more repositories. If you manage Red Hat content and upload a Red Hat manifest, Foreman automatically groups Red Hat content within products. If you manage SUSE content using SCC Manager plugin, Foreman automatically groups SUSE content within products. For more information, see Managing SUSE content in Managing content.
- Promote (a content view)
-
The act of moving a content view from one lifecycle environment to another. For more information, see Promoting a content view in Managing content.
- Provisioning
-
The provisioning of a host is the deployment of the base operating system on the host and registration of the host to Foreman. Optionally, the process continues with the supply of content and configuration. This process is ideally automated. Provisioned hosts run on compute resources or bare metal, never Foreman server or Smart Proxy servers.
- Provisioning template
-
Provisioning templates are templates that automate deployment of an operating system on hosts. Foreman contains provisioning templates for all supported host operating system families:
-
AutoYaST for SUSE Linux Enterprise Server
-
Kickstart for AlmaLinux, Amazon Linux, CentOS, Oracle Linux, Red Hat Enterprise Linux, and Rocky Linux
-
Preseed files for Debian and Ubuntu
-
- Publish (a content view)
-
The act of making a content view version available in a lifecycle environment and usable by hosts.
- Pulp
-
A service within Katello responsible for repository and content management.
- Puppet
-
Puppet is a configuration management tool utilizing a declarative language in a server-client architecture. For more information about using Puppet to configure hosts, see Configuring hosts by using Puppet.
- Puppet agent
-
A service running on a host that applies configuration changes to that host.
- Puppet environment
-
An isolated set of Puppet agent nodes that can be associated with a specific set of Puppet Modules.
- Puppet manifest
-
Refers to Puppet scripts, which are files with the .pp extension. The files contain code to define a set of necessary resources, such as packages, services, files, users and groups, and so on, using a set of key-value pairs for their attributes.
Do not confuse with Manifest (Red Hat subscription manifest).
- Puppet server
-
A Smart Proxy server component that provides a Puppet catalog to hosts for execution by the Puppet agent.
- Puppet module
-
A self-contained bundle of code (Puppet Manifests) and data (facts) that you can use to manage resources such as users, files, and services.
- PXE
-
PXE stands for preboot execution environment and is used to boot operating systems received from the network rather than a local disk. It requires a compatible network interface card (NIC) and relies on DHCP and TFTP.
- Recurring logic
-
A job executed automatically according to a schedule. In the Foreman web UI, you can view those jobs under Monitor > Recurring logics.
- Registry
-
An archive of container images. Foreman supports importing images from local and external registries. Foreman itself can act as an image registry for hosts. However, hosts cannot push changes back to the registry.
- Remote execution (REX)
-
Remote execution is the process of using Foreman to run commands on registered hosts.
- Repository
-
A repository is a single source and the smallest unit of content in Foreman. You can either synchronize a repository with a URL or manually upload content to Foreman. Foreman supports multiple content types. For more information, see Content types in Foreman in Managing content. One or more repositories form a product.
- Resource type
-
Refers to a part of Foreman infrastructure, for example host, Smart Proxy, or architecture. Used in permission filtering.
- Role
-
Specifies a collection of permissions that are applied to a set of resources, such as hosts. Roles can be assigned to users and user groups. Foreman provides several predefined roles.
- Salt
-
Salt is a configuration management tool used to maintain hosts in certain defined states, for example have packages installed or services running. It is designed to be idempotent. For more information about using Salt to configure hosts, see Configuring hosts by using Salt.
- SCAP content
-
SCAP stands for Security Content Automation Protocol and refers to
.xmlfiles containing the configuration and security baseline against which hosts are checked. Foreman uses SCAP content in compliance policies.
- Smart Proxy server
-
Smart Proxy servers can provide DHCP, DNS, and TFTP services and act as an Ansible control node, Puppet server, or Salt Master in separate networks. They interact with Foreman server in a client-server model. Foreman server always comes bundled with an integrated Smart Proxy.
Smart Proxy servers are required in Foreman deployments that manage IT infrastructure spanning across multiple networks and useful for Foreman deployments across various geographical locations.
- Subnet image
-
A type of generic image for PXE-less provisioning that communicates through Smart Proxy server.
- Subscription
-
An entitlement for receiving content and service from Red Hat.
- Subscription Manager
-
Subscription Manager is a client application to register hosts to Foreman.
subscription-manageruses activation keys to consume content on hosts.
- SUSE Subscription
-
You can use Foreman to manage SUSE content. For more information, see Managing SUSE content in Managing content.
- Synchronization
-
Synchronization describes the process of fetching content from external repositories into the Foreman server.
- Sync plan
-
Sync plans describe the scheduled synchronization of content from external content.
- Tailoring files
-
Tailoring files specify a set of modifications to existing SCAP content. They adapt SCAP content to your particular needs without changing the original SCAP content itself.
- Task
-
A background process executed on the Foreman or Smart Proxy server, such as repository synchronization or content view publishing. You can monitor the task status in the Foreman web UI under Monitor > Foreman Tasks > Tasks.
- Trend
-
A means of tracking changes in specific parts of Foreman infrastructure. Configure trends in Foreman web UI under Monitor > Trends. Requires foreman_statistics plugin on your Foreman server.
- Updating Foreman
-
The process of advancing your Foreman server and Smart Proxy server installations from one patch release to the next, for example Foreman nightly.0 to Foreman nightly.1.
- Upgrading Foreman
-
The process of advancing your Foreman server and Smart Proxy server installations from one minor release to the next, for example Foreman 3.18 to Foreman nightly.
- User group
-
A collection of roles which can be assigned to a collection of users.
- User
-
Anyone registered to use Foreman. Authentication and authorization is possible through built-in logic, through external resources (LDAP, Identity Management, or Active Directory), or with Kerberos.
- Virtualization
-
Virtualization describes the process of running multiple operating systems with various applications on a single hardware host using hypervisors like VMware, Proxmox, or libvirt. It facilitates scalability and cost savings. You can attach virtualization infrastructure as compute resources to Foreman. Enable appropriate plugins to access this feature.
- virt-who
-
An agent for retrieving IDs of virtual machines from the hypervisor. When used with Foreman, virt-who reports those IDs to Foreman server so that it can provide subscriptions for hosts provisioned on virtual machines.
- XCCDF profiles
-
Extensible configuration checklist description format (XCCDF) profiles are a component of SCAP content. XCCDF is a language to write security checklists and benchmarks. An XCCDF file contains security configuration rules for lists of hosts.
Appendix C: Help resources for using CLI in Foreman
Foreman offers multiple user interfaces: Foreman web UI, Hammer CLI, API, and through Ansible collection theforeman.foreman. If you want to administer Foreman on the command line, have a look at the following help output.
- Foreman services
-
A set of services that Foreman server and Smart Proxy servers use for operation. You can use the
foreman-maintaintool to manage these services. To see the full list of services, enter theforeman-maintain service listcommand on the machine where Foreman or Smart Proxy server is installed. For more information, runforeman-maintain --helpon your Foreman server or Smart Proxy server.
- Foreman plugins
-
You can extend Foreman by installing plugins. For more information, run
foreman-installer --full-helpon your Foreman server or Smart Proxy server.
- Hammer CLI
-
You can manage Foreman on the command line using
hammer. For more information on using Hammer CLI, see Using the Hammer CLI tool or runhammer --helpon your Foreman server or Smart Proxy server.